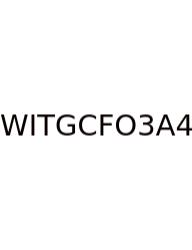40 Oz Of Water Is How Many Cups
40 Ounces of Water How Many Cups Is That and Why Does It Matter Knowing how much water you drink daily is crucial for maintaining good health Many people aim for the recommended eight glasses of water a day but what does that actually mean in ounces or cups This article dives deep into the conversio
Click here to continue reading this article...